Our Services
Cybersecurity that’s easy, effective, and to the point.
Start Today
Start Today
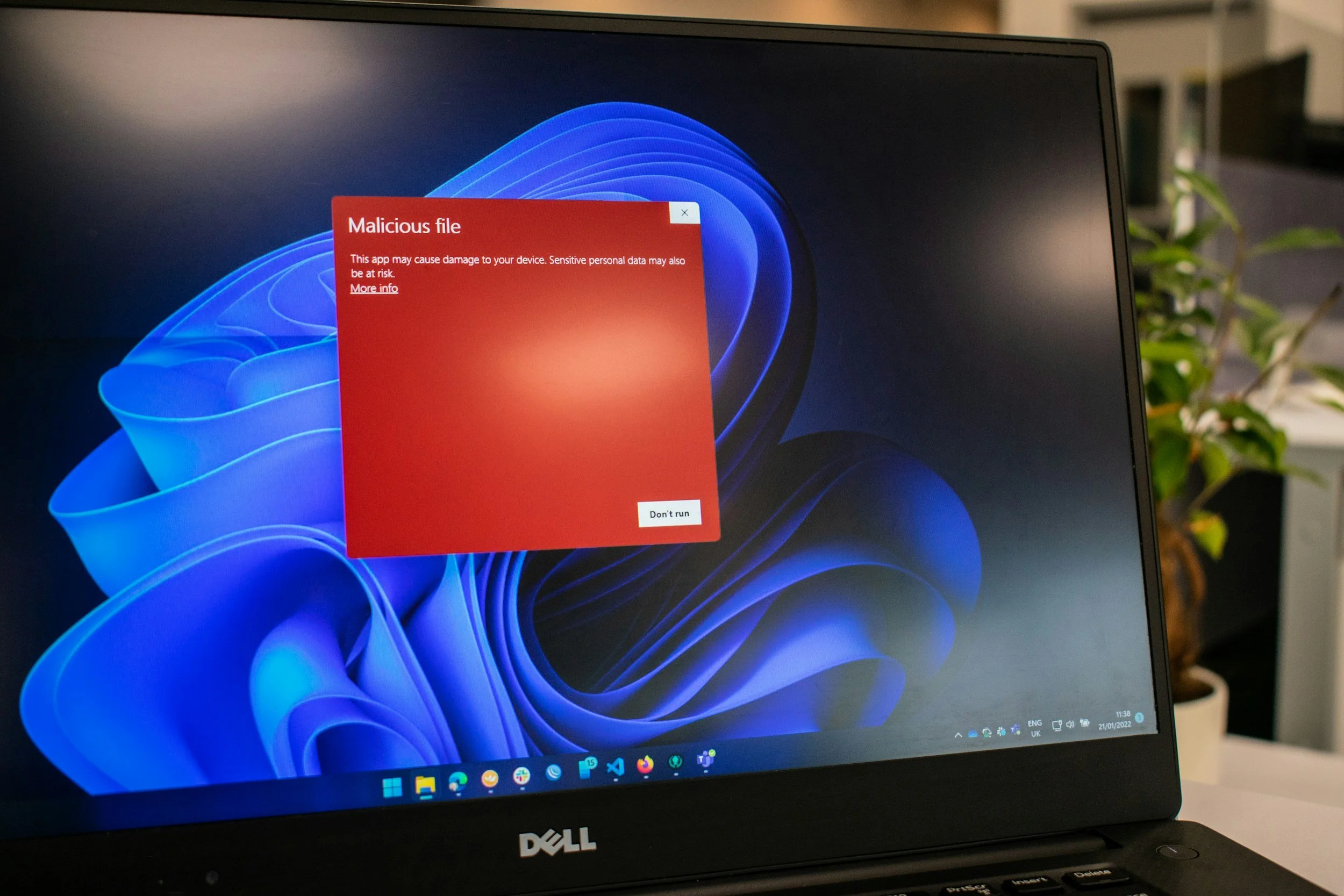
Email Security
Did you know that over 80% of companies don’t have DMARC configured in a restricted mode, leaving them vulnerable to email spoofing?
Our email security services help address this risk, providing:
Security Checkups: Identify vulnerabilities in Google and Microsoft mailboxes, tailored from basic to advanced needs.
Phishing Protection: Block phishing attacks before they reach your inbox.
Spam & Malware Filtering: Keep your inbox free of harmful attachments and unwanted messages.
Encryption & Compliance: Secure sensitive emails and ensure industry compliance.
Ongoing Monitoring: Detect suspicious activity in real time and provide regular security reports.
We make email security simple, scalable, and effective for any business.
Endpoint Security
Did you know that the average time to detect a breach is over 200 days, emphasizing the importance of proactive endpoint security measures?
Our endpoint security services provide comprehensive protection for your devices, including:
Deployment & Management: Complete setup and ongoing management of your endpoint security infrastructure.
Incident Response: Rapid detection and response to incidents, minimizing potential damage and downtime.
Scalability: Flexible solutions designed for organizations of all sizes and budgets, ensuring robust protection.
Custom Protection: Tailored security strategies to create the most secure device setup within your budget.
Continuous Monitoring: Ongoing monitoring to identify and respond to emerging threats in real-time.
With our endpoint security services, you can ensure your devices are always protected against evolving cyber threats.
Identity & Access Management
Did you know that the average person has around 100 accounts, with a significant number being vulnerable to compromise due to weak access controls?
Our identity and access management (IAM) services enhance security across cloud platforms, including:
User Authentication: Implementing strong authentication measures to ensure that only authorized users gain access to sensitive resources.
Role-Based Access Control: Tailored permissions based on user roles to limit access to critical data and applications.
Scalability: Solutions designed to accommodate organizations of any size, from startups to large enterprises.
Cloud Integration: Seamless integration with AWS, GCP, and Azure for comprehensive security across your cloud services.
Ongoing Monitoring: Continuous monitoring of access activities to detect suspicious behavior and ensure compliance.
With our IAM services, you can protect your organization against unauthorized access while managing user identities effectively.
Security Awareness & Training
Did you know that recognizing the signs of a cyberattack is the first step in preventing it?
Our security awareness and training services empower your team to identify and respond to threats effectively through:
In-Person Training: Customized sessions delivered directly to individuals or groups, focusing on real-world scenarios and practical skills.
Simulated Phishing: Ongoing phishing simulations to help employees recognize and respond to phishing attempts.
Online Training Modules: Engaging video content and interactive lessons to reinforce security best practices.
Tailored Curriculum: Training programs designed to meet the unique needs of your organization and industry.
Continuous Learning: Regular updates and refresher courses to keep your team informed about the latest threats and defenses.
By investing in security awareness and training, you can create a proactive culture that significantly reduces the risk of cyberattacks.
Book an appointment.
It all begins with an idea. Maybe you want to launch a business. Maybe you want to turn a hobby into something more. Or maybe you have a creative project to share with the world. Whatever it is, the way you tell your story online can make all the difference.